SSH Tunneling allows you "to force" your browser to connect to the internet via an encrypted connection. In other words, you can browse the internet securely so nobody will spy you. It means your IP address will be hidden from the outside and with some little config you also get your DNS request encrypted. It is a different thing compared with our latest OpenVPN and DNSCrypt guide. By SSH Tunneling, you get both internet line and DNS request encrypted in one blow. Yes, it is easy to do by just three steps. The only requirement is your SSH account. Please understand that I am not a phreaker or doing any phreaking stuff here. What actually we will do is to create SOCKS proxy and tunnel all connections via that SOCKS by using ssh.
1. Command
ssh -fCND 127.0.0.1:1080 yourusername@yourserver.com
- -f: this option tells SSH to run on background so you can close the Terminal safely.
- -C: compress all data.
- -N: tells SSH to do only tunneling and no command executed remotely.
- -D: use address IP:PORT like 127.0.0.1:1080 above.
- yourusername: change it with your SSH account username.
- yourserver.com: change it with your SSH server address.
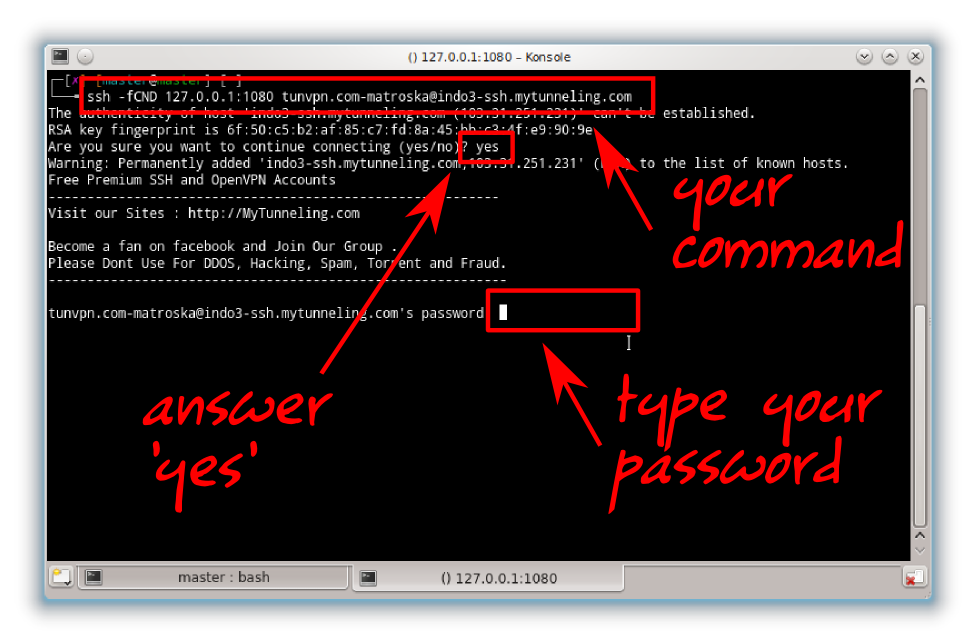
You may refer to man ssh to get more information. If your Terminal goes back to prompt after ssh command and login, then it means your ssh command is done. Check it by command ps aux | grep ssh.
2. Configuration
3. Test Your Connection
Yes, by just those two steps, you have your connection encrypted securely. To check it, simple ask for your IP address to Google. Or, use tcpdump to examine whether your connection is being forwarded or not.
- Google: type "what is my ip" and see that your IP is changed into the SSH server IP. Now, nobody knows you are you. They know only the SSH server, not you.
- Tcpdump: type command sudo tcpdump -i wlan0 (for WLAN) or sudo tcpdump -i eth0 (for LAN) or you may specify your own interface. See that tcpdump shows you that your connection is being forwarded to a new address which is your SSH server address.
Bonus
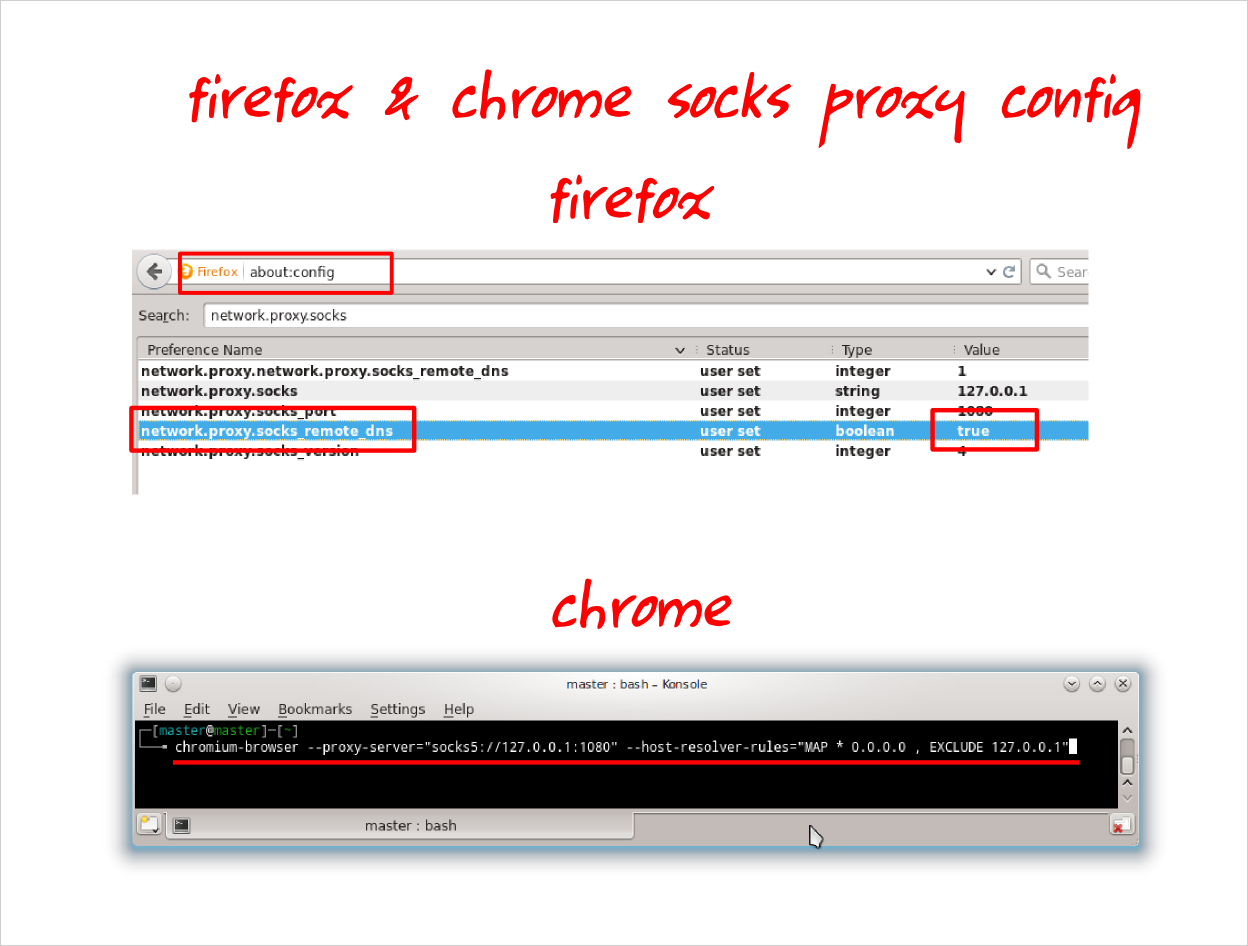
By just using those two steps, you get a secure connection (it is encrypted) but you have no DNS request encryption yet. This DNS request encryption is very useful so nobody will spy what you browse and you will be safe from DNS hijacking. How to do it? You can configure Firefox or Chrome to do that. Here the steps.- Firefox: open address about:config in address bar > search for network.proxy.socks_remote_dns > change the value into true.
- Chrome: close your chrome first > open Chrome via Terminal with complete command like this chromium-browser --proxy-server="socks5://127.0.0.1:1080" --host-resolver-rules="MAP * 0.0.0.0 , EXCLUDE 127.0.0.1"
Notes
- SSH tunneling or ssh port forwarding is very useful in security matter. You can browse any website anonymously. But you get more advantages, such as passing through the internet limitation by above DNS request encryption.
- I mentioned "browser" above doesn't mean that it is limited only for browser. Any other internet application such as email client, IRC client, torrent (if your server supports it), or whatever can use this SSH tunnel too. So as a summary, with SSH tunneling you get secure browsing plus secure IRC, email, torrent, download management, FTP, and so on. Just configure them to connect via SOCKS 127.0.0.1 port 1080.



